New “Freak” SSL exploit may be a major threat to online security
The name “Heartbleed” will ring a bell to almost anyone. It was center stage in a quite significant security crisys in 2014. In its essence, it was a fault that plagued the widely-used TLS (Transport Layer Security) protocol, used to protect HTTP connections. That problem was quickly dealt away with by an emergency patch to the OpennSSL cryptography library which contained the vulnerability.

News has come today that researchers have found another vulnerability in the same package, which could, once again, expose a lot of critical and personal data to malicious attacks. Just like Heartbleed, the new exploit, dubbed “FREAK attack” targets the SSL/TLS protocol, widely used for securing online connections. This new exploit, however is not solely limited to servers, but could put browsers at risk as well.
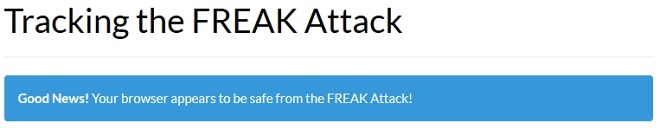
First things first. We tested whatever browsers we could get our hands on and you can rest assure that the current versions of Opera, Firefox, Chrome and even Internet Explorer are all secured and not vulnerable. You can check this website to see if your browser is secure. As far as we know, Apple’s Safari browsers might be vulnerable in certain versions, as well as the stock Android browser.
But you may be asking yourself how “FREAK” works, how is it different from Heartbleed and what dangers it holds? Well, while heartbeat was a server-side only bug which essentially allowed what is called a “buffer over-head” or in other words, reading beyond what you are supposed to read, “FREAK” is a man-in-the-middle attack. What it does is basically attempt to use a very outdated cipher suite, known as RSA_EXPORT, which is still present for backwards compatibility in a lot of OpenSSL packages, as well as many embedded devices.
A hacker can stand between a client and a server and request that the server send data in the outdated cipher. Once the response is captured, it is very straightforward to break what was adequate security in the 90s with current hardware. The same can be achieved in the other direction by cheating your browser, but it has to be susceptible to what is known as “CVE-2015-0204″, which is very unlikely, unless you are on a weird proprietary device. Better safe than sorry though.
As it turns out, a lot of websites are vulnerable to the bug, including banking sites and even U.S government sites. A lot of Apple’s products are also exposed to the threat, but like with the previous security panic, this does not necessarily mean anything bad is going to happen. While the security bug has been discovered, there are still no known attempts to exploit them for malicious purposes. There are already a few sites, dedicated to exposure assessment, so you can go to FreakAttack.com and check if any site you frequently visited is now kind of dangerous.
Apple has also promised that it will be shipping a security update to vulnerable devices very shortly. In the meantime hold tight, check and update your browser and check back for an update, when one becomes available.
Featured
Categories
- Mobile phones
- Mobile software
- Mobile computers
- Rumors
- Fun stuff
- Various
- Android
- Desktop software
- Featured
- Misc gadgets
- Gaming
- Digital cameras
- Tablets
- iOS
- Desktop computers
- Windows Phone
- GSMArena
com - Online Services
- Mobile Services
- Smart Watches
- Battery tests
- BlackBerry
- Social Networks
- Web Browsers
- Portable Players
- Network Operators
- CDMA
- Windows
- Headphones
- Hands-on
 Samsung Galaxy S6 updated to Android 5.1.1: exploring the differences on video
Samsung Galaxy S6 updated to Android 5.1.1: exploring the differences on video Oppo R7 battery life test
Oppo R7 battery life test Benchmarking Asus ZenFone 2 ZE551ML with Intel Atom Z3580 SoC and 4GB of RAM
Benchmarking Asus ZenFone 2 ZE551ML with Intel Atom Z3580 SoC and 4GB of RAM Hot or Not: Android M, iOS 9 and Watch OS 2.0
Hot or Not: Android M, iOS 9 and Watch OS 2.0 HTC One E9+ performance benchmarks
HTC One E9+ performance benchmarks
Comments
Rules for posting