[Updated] Samsung’s Smart TVs send unencrypted data over the Internet, researchers say
Last week, after it was discovered that Samsung’s smart TVs are potentially listening to everything that users say and sharing the collected information, a company spokesperson said, “In all of our Smart TVs we employ industry-standard security safeguards and practices, including data encryption, to secure consumers’ personal information and prevent unauthorized collection or use.” However, apparently that’s not correct, as it has now been discovered that the voice data these TVs send over the internet is not encrypted.
Update: Samsung is aware of the issue and is working on a fix. The company says that new models include encryption, while older devices will get it as an update.
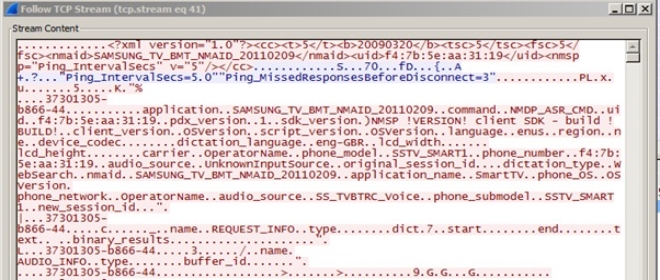
Researchers at security consultancy Pen Test Partners used network inspection tool Wireshark to capture and study the data transmitted by the South Korean company’s smart TVs, revealing that the information is sent over port 443, which is usually used for TLS-secured HTTPS connections, and typically not firewalled off. The information is transmitted in plain text, making it a ripe target for man-in-middle attacks.
“What we see here is not SSL encrypted data,” said researcher David Lodge in a blog post. “It’s not even HTTP data, it’s a mix of XML and some custom binary data packet.” The information that’s transmitted includes the TV’s MAC address, the version of the OS in use, and of course, the audio.
Even the data sent back by processing servers is also not encrypted, researchers said, adding that they were also able to decode the encoded voice audio, allowing them to replay the users’ spoken voice commands. “There’s plenty to suggest that interesting data is making its way on to the interwebs from your TV. Come on Samsung, how about at least protecting it with SSL?,” Lodge concluded.
Featured
Categories
- Mobile phones
- Mobile software
- Mobile computers
- Rumors
- Fun stuff
- Various
- Android
- Desktop software
- Featured
- Misc gadgets
- Gaming
- Digital cameras
- Tablets
- iOS
- Desktop computers
- Windows Phone
- GSMArena
com - Online Services
- Mobile Services
- Smart Watches
- Battery tests
- BlackBerry
- Social Networks
- Web Browsers
- Portable Players
- Network Operators
- CDMA
- Windows
- Headphones
- Hands-on
 Hot or Not: Android M, iOS 9 and Watch OS 2.0
Hot or Not: Android M, iOS 9 and Watch OS 2.0 Your verdict on Android M, iOS 9 and Watch OS 2.0
Your verdict on Android M, iOS 9 and Watch OS 2.0 Oppo R1x battery life test
Oppo R1x battery life test HTC One E9+ performance benchmarks
HTC One E9+ performance benchmarks Lenovo A7000 Preview
Lenovo A7000 Preview
Comments
Rules for posting